You might picture a device that hides your IP address and enables you to access internet material when you think of proxy server. Yet, that is simply one use for proxy servers. We will examine the many types and benefits of proxy servers in this article.
Proxy Server’s Definition
A proxy server is a computer or system that serves as a middleman between a web browser or other endpoint device and a destination server that provides the requested service.
The communication between the client and the requested service can be improved and made more secure using proxy servers. But, depending on your demands and the sort of proxy server you use, the precise functionality and security or privacy advantages may differ.
The Way a Proxy Server Functions (How IT Works)
The definition of the word “proxy” is “to act on behalf of another,” and a proxy server does just that. It receives and forwards requests on behalf of the client or web server.
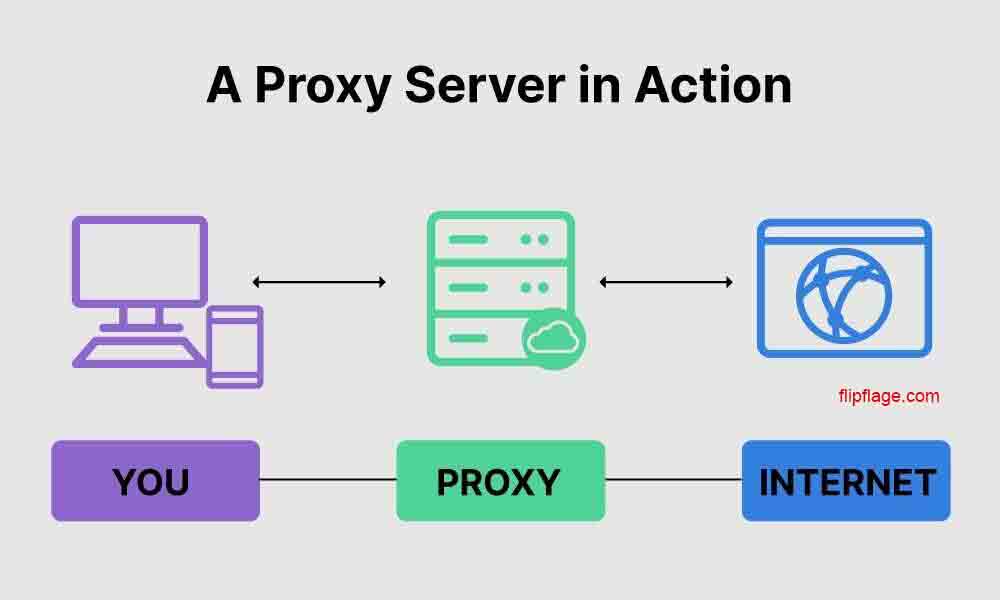
Prior to receiving the requested data, the request must first pass through the proxy server on its route to the requested address and again on its way back. More specifically, here’s how it functions:
- The client (your device or web browser) asks a destination server for web content or a service.
- The request first goes to the proxy server rather than the destination server directly.
- The proxy server verifies that the client’s request complies with established guidelines: (i) If it does, the proxy server on behalf of the client sends the request to the target server. (ii) If not, the proxy server may display an error message or reroute the client to a different server.
- The destination server responds to the proxy server after processing the request.
- The response can be modified by the proxy server. It might be cached for later use, filtered to remove objectionable content, or subjected to authentication checks before the client can view it, for instance.
- Eventually, the client receives the (modified) response from the proxy server. The client interacts with the service or views the web content as if it were directly linked to the destination server.
Virtual private network (VPN) servers and proxy servers both perform comparable functions. Additionally, they conceal your identity by routing communications on your behalf. A VPN and a proxy server vary most noticeably in that a VPN also encrypts the communication, whereas a proxy server does not.
The client may not be aware of the intermediary proxy and believe it is directly talking with the requested address because a proxy server can be on the server side or a component of the network infrastructure.
For instance, without your knowledge, your company’s network or internet service provider (ISP) may use a proxy server to cache or filter material, or even to track your online activities. And proxy servers are employed for other purposes as well.
What is the Purpose of a Proxy Server?
Proxies are effective tools for streamlining operations and safeguarding network traffic. The following are a some of the most typical uses for proxy servers:
- Filtering for Networks. Proxy servers can filter and restrict access to specific websites and online information. In this situation, proxies function similarly to firewalls, enforcing compliance and internet censorship, guarding against phishing and malware assaults, and limiting access to inappropriate or unlawful content.
- Caching. Web pages, photos, and videos are regularly requested resources that are stored on proxy servers. Then, rather than having clients request content from the originating server, they serve clients cached data.
- Balanced load. To avoid overtaxing one server, proxy servers split up client requests among several servers. They can also identify malfunctioning or overburdened servers and reroute queries to underutilized servers.
- Avoiding Constraints. Client-side proxies can assist in getting around internet limitations whereas proxy servers on the server can impose them. Proxy servers can get beyond limitations imposed by network administrators, ISPs, or even governments since they reroute web traffic.
- IP address masked. Your IP address is hidden from the web destination because the proxy server establishes a connection on your behalf.
It shields your IP address and other personal data from the websites you visit online. - Encryption and decryption for SSL. Certain varieties of proxy servers support SSL/TLS encryption and decryption. It enables the web server to concentrate on handling requests as opposed to managing cryptography.
- Routing. Based on predetermined criteria, such as the content of the request or the location of the client, a proxy server can route requests through several servers.
Proxy Server Types
Based on their features and protocol usage, proxy servers can be divided into a number of different groups. Here, we’ll examine the most typical kind of proxy servers.
Proxy servers according to traffic
The most typical classification of proxy servers takes into account the flow of traffic as well as the proxy’s position in respect to clients and servers. It distinguishes between forward and reverse proxy servers.
Reverse Proxy: A reverse proxy is a proxy server that responds to client requests on behalf of the web server. A reverse proxy is also referred to as a server-side proxy because it is situated on the server’s network.
While the client perceives the reverse proxy as the web server, the web server sees the reverse proxy as the client. A proxy server plays a crucial part in assuring the dependability, security, and efficiency of web applications by assisting the web server in remaining concealed from clients.
Reverse proxies are useful for load balancing, caching, and security on servers. Reverse proxies can also offer a solitary access point to numerous web servers, simplifying the scaling and management of web applications.
Forward Proxy: A forward proxy is a proxy server that requests resources from the internet on behalf of the client. The forward proxy is also referred to as a client-side proxy because it is situated on the client’s network.
While the client perceives the forward proxy as the internet, the internet perceives the forward proxy as the client. Forward proxies enable users to access blocked websites, obfuscate their identity and IP address, and get around content filters.
Proxy Servers by Origin
Based on their location and operators, proxy servers can also be categorized.
Residential Proxy: A residential proxy is an intermediary server with an IP address that has been given to a house or company by an internet service provider (ISP).
If you allow an outsider to send traffic through your computer, it may act as a residential proxy. In that situation, you would be the residential proxy’s owner and it would have your device’s IP address.
Web scraping, data mining, ad verification, and other online operations requiring strong anonymity and IP rotation are among the purposes of a home proxy. Residential proxies are typically more trustworthy than other proxy kinds since they mimic the actions of real people using the internet. Unfortunately, such proxies are also more expensive to get and keep up.
Proxy Data Center: An intermediary server that is hosted in a data center and is usually configured expressly for proxying web traffic is known as a data center proxy. High-volume web scraping and automation operations are some of its uses.
Residential proxies are far more difficult to get and maintain than data center proxies. They are also speedier and more stable, but because of their predictable behavior, websites and search engines are better at identifying and blocking them.
Mobile Proxy: An intermediary server that is hosted on a mobile device, like a smartphone or tablet, and has its IP address issued by a mobile carrier is known as a mobile proxy. Mobile app testing and mobile ad verification are two applications for the mobile proxy.
Proxy Servers by Level of Anonymity
Your browsing can become more private by using a proxy server, although the degree of anonymity varies based on the proxy server type.
Transparent Proxy: An intermediary server known as a transparent proxy does not conceal the IP address of the client.
Using transparent proxies won’t make you anonymous. They are useless for increasing online privacy because they reveal your identity to the server. They do, nevertheless, have a purpose. Transparent proxies can be used for caching to make your online browsing go more quickly. Lowest Level of anonymity:
Anonymous Proxy: The IP address of the user is concealed from web servers through an intermediary server known as an anonymous proxy. But, the anonymous proxy may also provide other details, such as the client’s operating system, language preferences, or browser type. Although it doesn’t directly identify you, this information aids in reducing the number of possible users. Medium level of anonymity.
High-Level Anonymity Proxy: An intermediary that conceals the user’s IP address and other identifying information sent in the HTTP headers, such as browser or operating system, is a high anonymity proxy server.
It is more challenging to link your activity to your IP address or device when using high anonymity proxies. It’s a respectable option among proxies for activities that call for privacy. Maximum level of anonymity.
Distorting Proxy: An intermediary server known as a distorting proxy conceals the client’s IP address and gives the server a fictitious IP address. Medium to high level of anonymity (depending on proxy server settings).
Rotating Proxies: In order to enable anonymity and avoid IP blocking, a rotating proxy is a server that acts as an intermediate and periodically rotates a pool of IP addresses. Web scraping, data mining, and other operations that call for sending a lot of queries to a server covertly can benefit from rotating proxies.
Anonymity level: modest to high (depends on the number of IP addresses in the pool and how often they are rotated).
Proxy Servers by Accessibility
Another way to categorize proxies is according to their accessibility.
Public Proxy: Everyone can access a proxy server that is public. It is accessible without requiring you to complete authentication. Public proxies naturally become slower and less dependable as a result of such accessibility. They are more likely to be banned and blocked from access to websites and search engines.
Shared Proxy: A shared proxy server is one that has numerous users. They have the same IP address and port, but different software and hardware setups keep their online activity separate. Another name for it is a semi-dedicated proxy.
Since shared proxies are private, accessing them requires authentication. They become quicker and more dependable than open proxies as a result.
Private Proxy: A private proxy is a proxy server that is solely utilized by one person or group. Private proxies are sometimes known as dedicated proxies since they give the user a dedicated IP address and port.
A better level of anonymity, security, and performance is provided via private proxies. They are more expensive than shared proxies and require authentication to access.